news
Defending Savannah from DDoS attacks
Quoting: Defending Savannah from DDoS attacks —
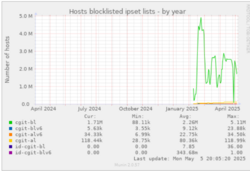
Savannah is under heavy attack, likely from one or more organizations using a massive botnet to build a dataset for training large language models (LLMs). Since January 2025, a distributed denial-of-service (DDoS) attack has been underway. With metrics for our IP blocklist reaching five million in February 2025. In this article, we will introduce Savannah and some tools and techniques that the Savannah hackers and FSF system administrators use to mitigate DDoS attacks against GNU resources and the FSF network. This series of attacks is not limited to Savannah: staff and volunteers have read about similar attacks against other software forges including Sourceware, Pagure, GitLab instances, SourceHut, and Codeberg, as well as Gitea and Forgejo instances. We hope this article can help others fight these attacks as well.
GNU Savannah is the software development forge operated by the GNU Project and hosted by the FSF. GNU Savannah was initially a fork of SourceForge installed by Loïc Dachary, distinguished by an express commitment to only host free software. While savannah.gnu.org is reserved for official GNU packages, savannah.nongnu.org hosts free software packages that are not officially GNU packages. Savannah is hosted by the FSF with a core infrastructure in Massachusetts, maintained and operated by the Savannah hackers team with the help of the FSF system administrators. Savannah continuously works to maintain an A-grade from the GNU Ethical Repository Criteria Evaluations.