Security: RC4, Clown Computing, and OpenSSL Headsup
-
RC4 Is Still Considered Harmful
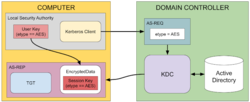
I've been spending a lot of time researching Windows authentication implementations, specifically Kerberos. In June 2022 I found an interesting issue number 2310 with the handling of RC4 encryption that allowed you to authenticate as another user if you could either interpose on the Kerberos network traffic to and from the KDC or directly if the user was configured to disable typical pre-authentication requirements.
This blog post goes into more detail on how this vulnerability works and how I was able to exploit it with only a bare minimum of brute forcing required. Note, I'm not going to spend time fully explaining how Kerberos authentication works, there's plenty of resources online. For example this blog post by Steve Syfuhs who works at Microsoft is a good first start.
-
4 Reasons Open Source Matters for Cloud Security
When we depend on an open commons as our computing foundation, we need it to be secure, and the most effective way to do that is through open solutions.
-
OpenSSL warns of critical security vulnerability with upcoming patch | ZDNET
We don't have the details yet, but we can safely say that come Nov. 1, everyone -- and I mean everyone -- will need to patch OpenSSL 3.x.